Legal Use Cases & Risk Tiers
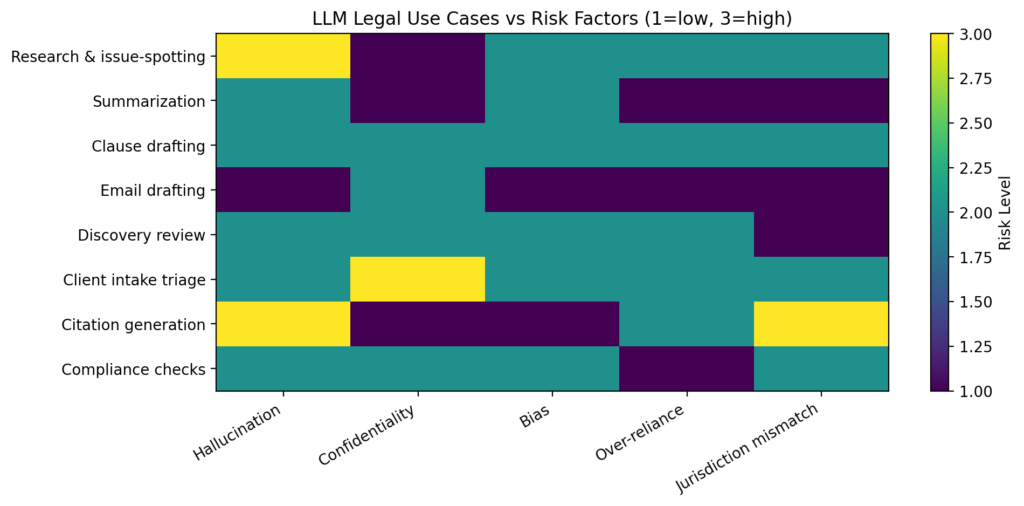
Not every use case has the same risk. The key is to match the tool to the task and add controls where the stakes are high.
Key takeaways
- Match the tool to the task: higher stakes require more controls.
- Treat citations as untrusted until verified.
- Avoid putting sensitive client data into public AI tools.
Low-risk, high-value tasks
- Drafting internal outlines
- Summarizing a provided document (you supply the text)
- Creating checklists and workflows
Medium-risk tasks (require verification)
- Drafting a client email (must review facts and tone)
- Generating a first-pass issue list for a motion
- Spotting missing clauses in a contract (still verify)
High-risk tasks (do not delegate judgment)
- Final legal conclusions
- Novel or unsettled legal questions
- Anything involving confidential client data in an unvetted system
Your risk controls toolkit
In later modules, you’ll learn controls such as: jurisdiction constraints, required citations, explicit uncertainty, step-by-step checklists, and external verification.